1. Backup Your Site
Always backup your site before tweaking its core files. There are two ways to do this, depending on whether or not you’re locked out of your site.
If you’re unable to login, you can save a copy of your site’s root folder via your hosting file manager or FTP. Here’s how:
- File manager – click on the site root directory and select compress. Once done, save it to your computer and download it.
- FTP – go to Control panel -> FTP and then download the folder using the same method as used above. The only difference is that you’ll need to use an FTP client like FileZilla.
Meanwhile, if you still have access to your site, you can use plugins such as UpdraftPlus, Backup Buddy, or VaultPress to save time.
Last but not least, keep a backup of your database stored locally as well.
2. Run a Scan on Your Computer
We suggest downloading your backup using an FTP client or with the file manager then locally running a scan on the backup.
Use an anti-virus system and a malware scanner such as Kaspersky or Malwarebytes to diagnose and fix possible issues in your site’s files. If the scan is successful and helps locate and remove any issues, change your FTP password and re-upload site files.
3. Remove the Malware Infection
There are a few actions you can take to remove malware from your WordPress site. First, you will need to access the site’s files through FTP or a file manager.
Erase every file and folder in your site’s directory except for wp-config.php and wp-content.
Afterward, open wp-config.php and compare its content with the same file from a fresh installation or wp-config-sample.php that can be found on the WordPress GitHub respository. Look for strange or suspiciously long strings of code and remove them. It’s also a good idea to change the password of your databases once you’re done inspecting the file.
Next, navigate to the wp-content directory and perform actions on these folders:
- plugins – list all your installed plugins, and erase the subfolder. Later you can re-download and re-install them.
- themes – delete everything except your current theme and check for suspicious code, or just remove it altogether if you’ve saved a clean backup or don’t mind reinstallation.
- uploads – check for anything you haven’t uploaded.
- index.php – after you’ve deleted the plugins, erase this file.
4. Download a Fresh WordPress Copy to Install
Re-download WordPress and re-upload the content to your website via FTP or the file manager.
Go to your file manager, click Upload Files, and locate the WordPress zip file. After it’s finished uploading, press the Extract button and enter a directory name to define the save location. Copy everything else besides the zip file to the site root folder.
Alternatively, you can use APP installer and edit the database credentials in the wp-config.php file to point it to your new installation.
5. Reset WordPress Password
If multiple users are running a website, the breach might have occurred through one of their accounts. It’s recommended to reset every user’s password, log out every account, and to check for any inactive or suspicious user accounts that should be deleted.
Change the passwords into long, randomized strings that can’t be breached by brute force attacks. It’s a great idea to use a password generator.
6. Re-Install Plugins and Themes
Now that you have removed malware from your WordPress site, re-install all the removed plugins and themes you had. However, be sure to leave out plugins that are outdated and no longer maintained.
While you’re at it, we advise you to install security plugins that can protect your WordPress site and easily remove malware in the future. Use one with a proven track record such as MalCare, WordFence, or Sucuri.
How to Remove Malware from WordPress Using a Plugin?
If you prefer a quicker way to remove malware from your site and can afford a premium service, you can purchase a WordPress security plugin.
For this article, we’re going to demonstrate how to remove malware from a WordPress site using Sucuri. But first, let’s take a look at what it offers:
- Server-side scanning (premium) and remote scanning (free). The latter only detects on-site malicious code and while the former also checks for it on the back-end.
- Detects compromised WordPress files in your system and replaces infected ones with their original copies.
- Runs a check on antivirus software and search engine databases to see whether your site is blacklisted.
- Reinforces your site’s security to prevent malware attacks.
- Notifies you whenever signs of malware activity are spotted.
- Sets up a firewall on your website (premium).
You can get Sucuri from the WordPress plugin repository.
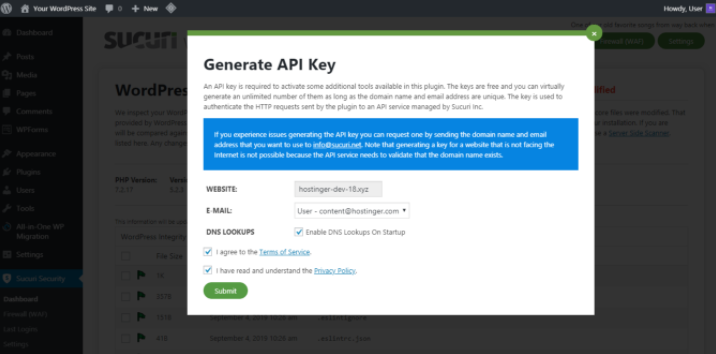
Once it is installed, you’ll need to go to the plugin’s dashboard and Generate an API Key to activate its features fully.
After your site is integrated with Sucuri’s API service, go to Dashboard -> Refresh Malware Scan. It will display a file log with any suspicious ones flagged. For this tutorial, we added suspicious code to our test site’s index.php file.
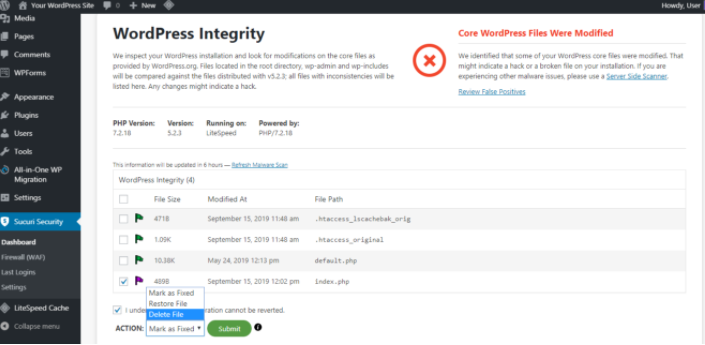
After running the scan, the file was flagged. You can select it and perform whichever action you prefer.
Removing the Warning Label on Google SERP
Although the malware has been removed from your WordPress site, you still need to ask Google to remove the site’s warning label:
- Access the Google Search Console and register your website. Skip to the third step if you have an account.
- After that, verify it either using Domain or URL prefix.
- Scroll down to find Security & Manual Actions on the left tab. Click to reveal a dropdown and select Security Issues.
- You will see the report on your site’s security, in which you can choose Request a review.
You must double-check whether you successfully remove malware from your WordPress site before submitting a request. Otherwise, it will get pinned as a repeat offender, and you won’t be able to request another review for 30 days.
Conclusion
Malware can be a major issue that removes all credibility and trust from your WordPress site while compromising you and your users. While reviewing how to remove malware from a WordPress site, we showed you two methods:
Manual removal, for which you need to:
- Back up your site.
- Use anti-virus and malware scanning software on the backup locally.
- Eliminate malware by tweaking your WordPress files and deleting old or suspicious ones.
- Reset all user passwords and check for suspicious users.
- Reinstall plugins and themes.
Or you can use plugins to fix the issues and improve your site’s security. Additionally, we also learned how to remove the warning label that can get placed on your website by Google.
With these actions in mind, hopefully, you can restore your WordPress site ASAP and keep future threats at bay.